APIM on internal mode is probably the most difficult implementation of them all.
Although there is loads of documentation and guides there are a number of things that are not mentioned anywhere. The most basic and simple fact is that if you try to spin up an APIM on internal mode on Azure it will just fail. So in order to do so you need to configure your V-net prior to building the service its self.
There are three services that must be configured prior to the APIM its self so that it can be provisioned successfully.
1)V-Net
2) NSG
3) Routing table
4)Private DNS
V-net
If you didn’t believe in this blog and tried to provision an APIM on an internal V-net then you already have a Vnet implementation but you do now know that that will fail. It is recommended that port 3443 will be allocated as ANY as shown in the NSG section. If you did go forward and implemented or you have deleted your resource group you will need to spin app a Vnet and a subnet in it. It is recommended that the minimum range of the subnet is /25.
NSG
Every V-Net needs an NSG to control port access on the network. In order for the APIM to be able to install all the necessary services there are a number of ports that needs whitelisting on the NSG.
The screen shot below show the inbound configuration on the NSG:
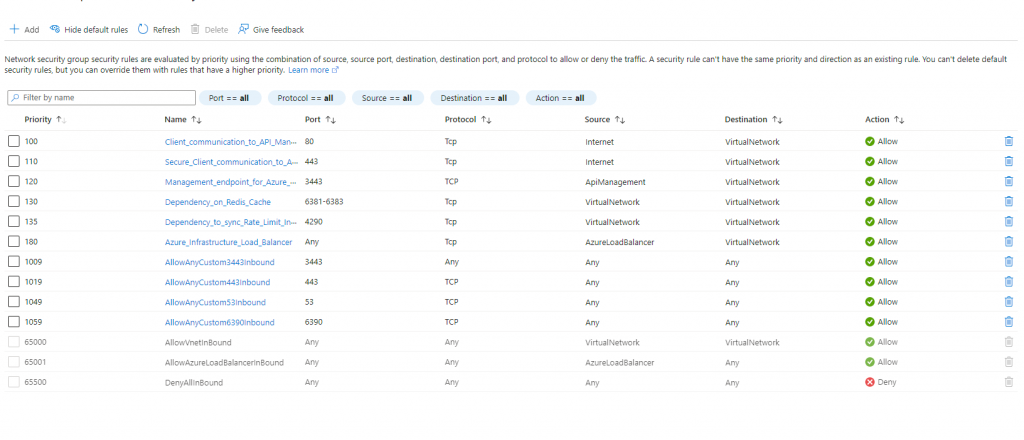
The inbound ports are : 443,3443,6381-6383,6390,4290,53. There is a lot of discussion of failing ports etc on a number of Blogs. As a hint it is suggested that 3443 port allocation should be configured as ANY in protocol, source and destination.
The outbound port whitelisting is shown below:
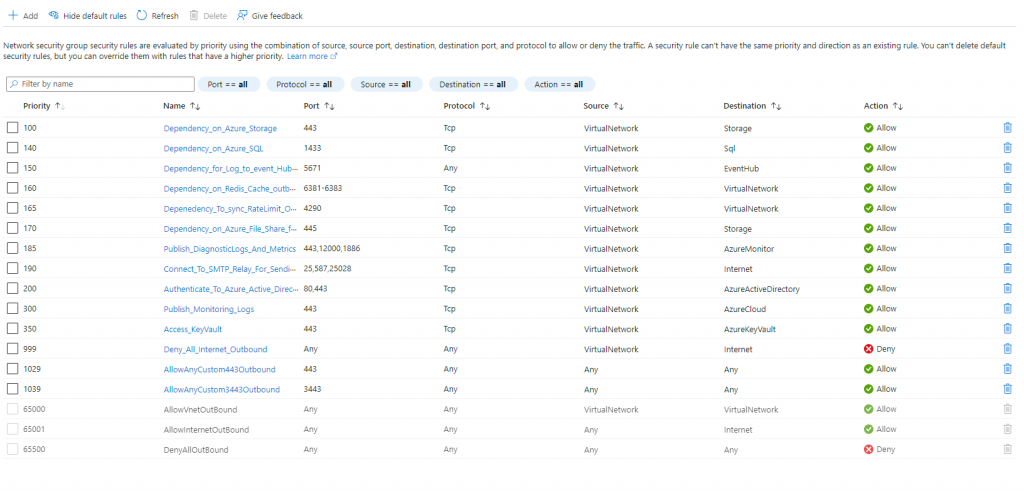
The outbound configuration is relative to every implementation. The ports above have been configured as part of accommodating a PowerPlatfotm integration. Those ports are: 443,1433,5671,6381-6383,4290,445,12000,1886,25,587,25028,3443. Again on 443 and 3443 the ANY allocation has bene added since the service tags specific allocation is playing up most of the time.
The above NSG configuration unleashes the full wraith of APIM. It is ready to integrate with all the back end services required and that APIM can utilize. There are a lot of guides out there that describe basic implementations or access to services.
Routing Table
All the above will not work with a routing table. We need to tell the internal services how to find their way to their destination in order to activate. Apim uses a number of services that we need them to be accessible so that the API manager can run successfully.
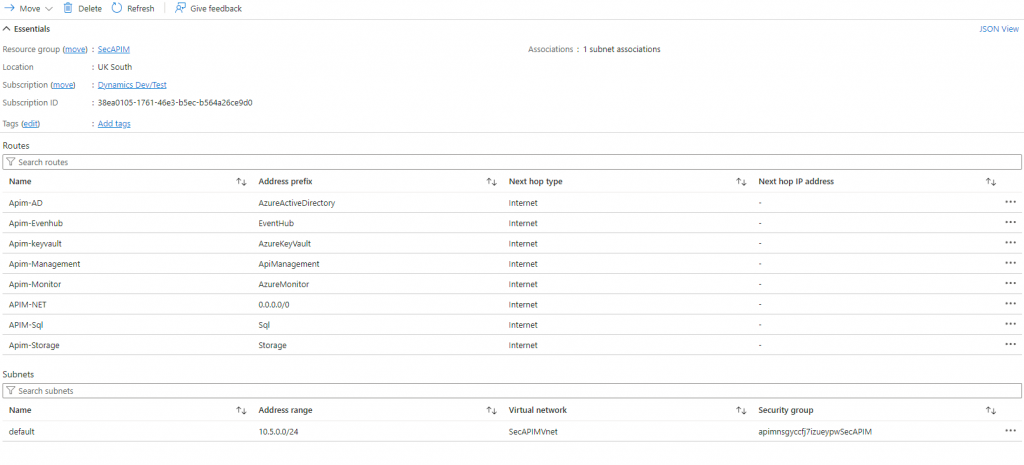
The service tags that needs to accees the internet are:
Azure active directory ,EventHub, Azure KeyVault, ApiManagement, AzureMonitor, Sql and storage as shown above.Do not forget to associate the routing table with the subnet. By adding 0.0.0.0/0 will help later on to access APIM from the internet.
Private DNS
Finally adding a private DNS zone will mitigate any resolving issues. This is the point where a name for the APIM must be chose since this will be used by default for the out-of-the-box gateway.In nay case add a private DNS zone under the name azure-api.net.
You are now ready to spin up an azure APIM by choosing the above V-net on internal mode to inject it in.
The service should look like that in the network tab:
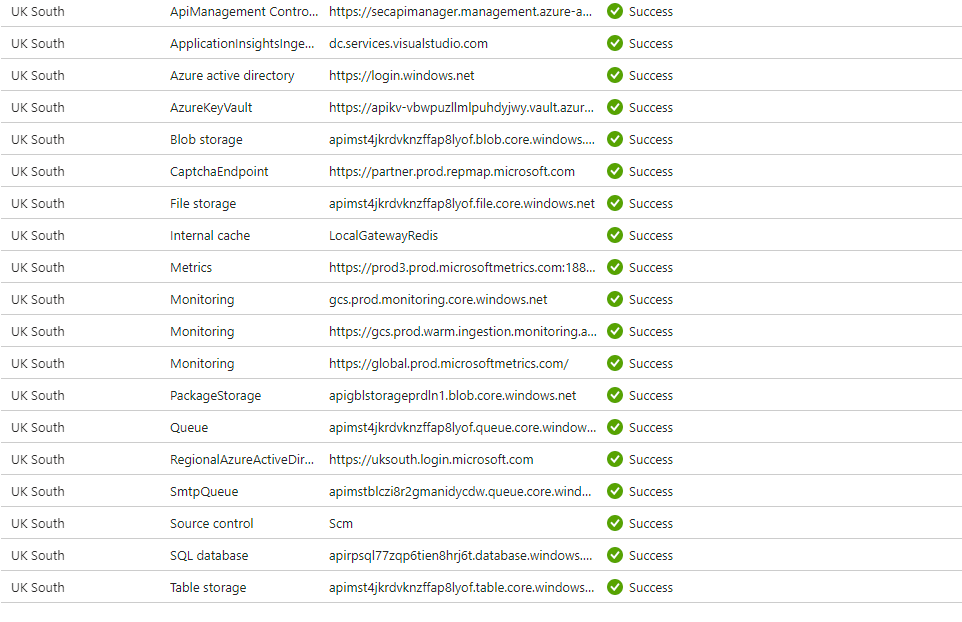
To further expand this implementation keep reading here on how to add an application gateway in front of the service so that you can integrate with other services-platforms like the PowerApps.